Introduction 🔗
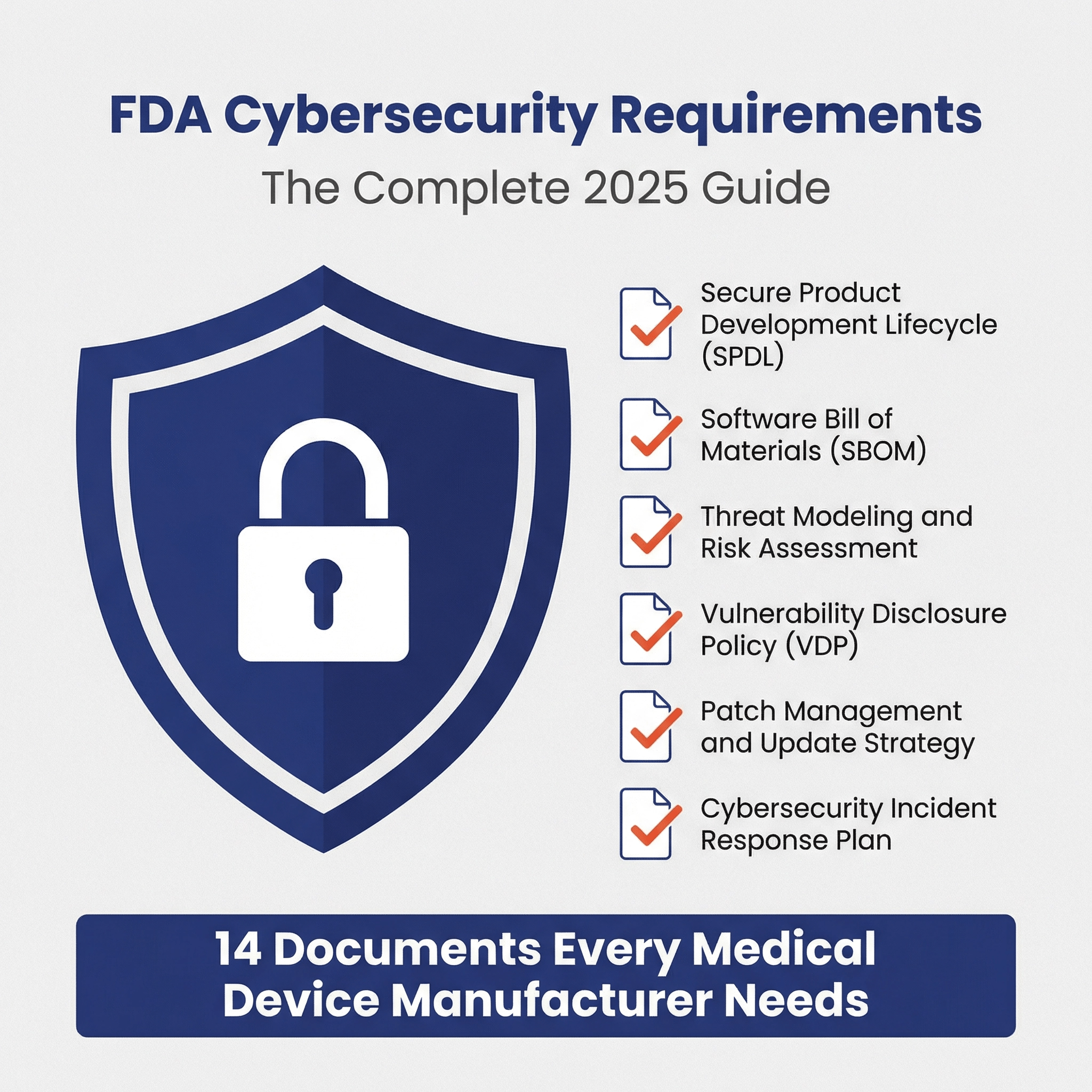
FDA has become increasingly strict regarding FDA cybersecurity. Any medical device that connects to the internet or has USB ports will require cybersecurity documentation and testing. This questionnaire will help you evaluate the state of your FDA cybersecurity readiness for an upcoming 510(k), De Novo, or PMA submission. It should be completed by a technical software lead on your team.
Each section includes percentage complete estimates. These are meant to give you a feeling for the size of the task involved. The actual effort involved will vary based on the nature of your device and your team’s experience.
Threat Modeling (20%) 🔗
- We have a threat model.
- It enumerates the assets included in the system, such as security keys, PHI, etc.
- It shows all of the internal and external connections from the medical device system.
- It considers the environment in which the device will be used.
- It considers threats to the software development lifecycle (e.g., vulnerabilities introduced into dependencies).
- It includes a diagram showing how software updates are propagated from code to the device.
- It includes diagrams for various “use-cases” of the device (e.g., different configurations, platforms, workflows).
SBOM (5%) 🔗
- We have put together an SBOM.
- We have a process for generating SBOMs quickly for new software releases.
- Our SBOM includes details about end-of-support dates
Cybersecurity Testing (25%) 🔗
- We have included cybersecurity controls in our software requirements specification.
- All our cybersecurity controls trace to design verification.
- We scanned our dependencies for cybersecurity vulnerabilities.
- We have completed appropriately-scoped, independent penetration testing.
Security Risk Management (10%) 🔗
- We have a documented procedure for security risk management.
- Our security risks trace to safety risks.
- We’ve have a documented plan for how to evaluating the severity and likelihood of security risks.
Cybersecurity Controls (25%) 🔗
- Our software development team has engineers who have experience/training in cybersecurity.
- We’ve reviewed the recommended cybersecurity controls in Appendix 1 of the FDA cybersecurity guidance, and have controls for the following categories (or have justifications as to why they don’t apply):
- Authentication
- Authorization
- Cryptography
- Code, Data, and Execution Integrity
- Confidentiality
- Event Detection and Logging
- Resiliency and Recovery
- Firmware and Software Updates
Cybersecurity Labeling (10%) 🔗
- Our user and/or operator manuals address have been written with cybersecurity in mind.
- They describe user behavior required to ensure secure use and configuration of the software.
- They describe how to install software or firmware updates.
- They explain how to get access to an SBOM in a timely manner.
- They describe backup and restore features.
- They describe methods for retention and recovery of device configuration.
- They explain how to react in the case of a possible exploit, including how to access log files.
- They address how to decommission software and PHI.
Misc. (5%) 🔗
- We’ve documented any known vulnerabilities that aren’t addressed.
- We’ve documented what metrics are used to evaluate our cybersecurity program (e.g., speed to patching vulnerabilities).
- We have a plan for on-going vulnerability monitoring and patching of the software with timeline goals.
Conclusion 🔗
I hope this evaluation is useful for you! You may want to checkout a few of our related resources.
Also, if you could use professional support securing your device and validating it for an FDA submission, please take a look at our FDA Cybersecurity Remediation Solution.