Introduction 🔗
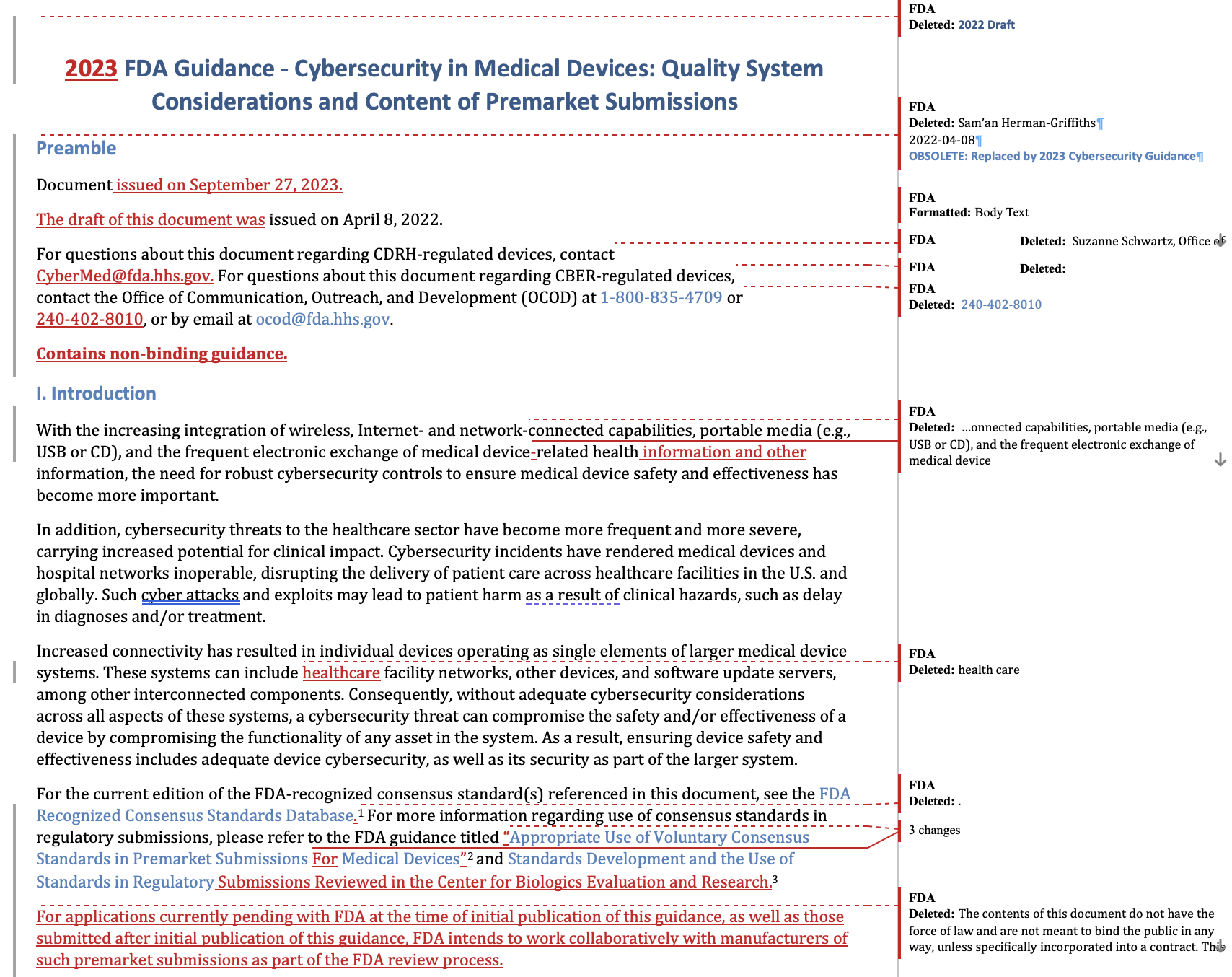
In recent years, the FDA has been amplifying its focus on cybersecurity, with its last final guidance rolled out in 2014. While a draft guidance surfaced in 2018, it remained unfinalized. Fast forward to 2022, another draft emerged, culminating in its finalization on September 27, 2023.
Many of our clients and readers are asking themselves: What’s changed in the final guidance? There are many online posts summarizing the changes, but I think for many professionals in the field, nothing beats a redline, letting you see all of the nuanced changes the FDA has made in the last year and a half.
Unfortunately, nobody (as best I’m aware) has a redline version. This is because the guidance is published as highly-formatted PDFs.
We can draft or review your cybersecurity documentation against the new guidance. We’re a team of medical-device software engineers with regulatory experience—we speak software and regulatory, and can save your engineer’s time and headaches by finding the simplest path to compliance.
How We Created the Redline 🔗
At Innolitics, we meticulously transcribe many FDA Guidance PDFs into HTML. We do this so that we can hyperlink specific sections when communicating with our clients (we’re always looking for ways to save engineers time and let them focus on building software, and not reading long regulatory documents).
For example, you can view the HTML transcript for the 2023 Cybersecurity Guidance here.
Our process for creating these redlines has been refined over the years, and involves a second cross-check and some automated checks. Even so, mistakes slip through. If you find any, let us know and we can correct it!
Leveraging our transcripts, we've created redline version of the 2022 guidance! You can download a copy at the end of this article.
In the following section, we summarize the key changes to the 2023 guidance.
Summary of Changes 🔗
Here is a somewhat detailed summary of the changes:
- Introduction of "cyber device" definition: Added “cyber device” definition per section 524B(c) of the FD&C Act.
- Confirmation of applicability: Clearly stated that the guidance applies to biological products, including Biologic License Application (BLA) and Investigational New Drug (IND) submissions.
- Cybersecurity scope: Clarified scope to include firmware and hardware, not just software.
- Risk analysis references: Updates mentions of risk analysis to the overall risk management file, which comports with recommendations in the 2023 FDA Guidance “Content of Premarket Submissions for Device Software Functions”
- Prohibited act clarification: Clarifies that failure to comply with section 524B(b)(2) requirements is considered a prohibited act under section 301(q) of the FD&C Act.
- Quality system integration: Emphasized the integration of security risk management throughout the entire quality system throughout the TPLC, not just integration into specific QSR processes (i.e., design controls, validation of production processes and CAPA).
- Safety and security separation: Recommended separate assessments for safety and security risks.
- Expanded threat modeling: Expanded the scope of threat modeling to include monitoring and responding to threats, not just prevention and mitigation.
- Interoperability consideration: Suggested considering interoperability in cybersecurity considerations.
- SBOM requirement: Clarified that a Software Bill of Materials (SBOM) is required for cyber devices.
- Identifying Vulnerabilities: Referenced CISA's Known Exploited Vulnerabilities Catalog for identifying vulnerabilities.
- Architectural views: Clarified that redundant documentation is not needed for security architectural views when one view adequately covers the risk of another. Additionally, if a view is not applicable a justification must be provided.
- Cybersecurity management plan: Broadened scope of recommended vulnerability communications to now include a full cybersecurity management plan.
- Cryptographic algorithm guidance: Advised against deprecated or disallowed cryptographic algorithms and recommended FDA pre-submission discussion for legacy algorithms.
- Appendix addition: Added an additional appendix, "General Premarket Submission Documentation Elements and Scaling with Risk" (Appendix 4), which includes a summary table of necessary cybersecurity documentation elements. The depth of documentation is expected to vary with security risk level (particularly in the case of threat modeling and architectural views), but the same elements are recommended for all risk levels.
- Added definitions: Included additional definitions in Appendix 5 such as anomaly, attack surface analysis, boundary analysis, fuzz testing, and uncontrolled risk.
Download 🔗
We hope this serves as a valuable asset to your team in your mission to better lives.
Click below to download the redline word document:
Innolitics_FDA_Cybersecurity_Guidance_Redline.docx
This is the first time we’ve published a redline! If you find it useful, please let us know by contacting us in the chat!

